If we want to turn off the computer, usually through the facilities Shutdown or Turn Off the usual accessed through Start - Turn Off Computer. There is one that allows us tips can turn off and turn on the computer with a fast, faster than normal booting process, Shutdown or Turn Off. Windows XP has a feature called Hibernate. We enable them to live alone.
At work, the computer data are processed temporarily stored on the memory. Hibernate is where the technology when the computer is turned off so that the data in memory 'transferred' to the hard disk. If a computer starts up again when the data are dihardisk 'restored' to the memory. URU ignite the process (booting) and held off the computer quickly because the computer does not take data from hard drives, but from memory.
Other functions of the computer Hibernate will display the latest applications that are run when the computer is turned off. For example, when we want to turn off the computer via Hibernate, when the application is running that is not. So when the computer starts up again, Winamp application is still open, more practical, right?
Hibernate how to activate the facilities are as follows:
* Right-click the desktop and select Properties
* Click the Screen Saver tab and then click the Power button ...
* Click the Hibernate tab. Tick ceklis on the option Enable hibernation. If you have, click OK
If we want to turn off the computer, click Start - Turn Off Computer. Once the box appears, press the Shift key. Note the picture with writing Stand by changes to Hibernate. Click the button and the computer will die more quickly. When we turn on the computer again, the process of booting it will run faster than usual.
Saturday, November 15, 2008
Save Data 'My Documents'
Almost all people to save the data in the My Documents folder. This folder is the standard folders from the computer to store our various documents. There is one more tips that we can save the data in the My Documents folder, the loss of data so that we can avoid early as possible.
Please note that the location of 'original folder' My Documents from this are in the C: \ Documents and Settings \ User name \ My Documents. You can click through mengeceknya right in the My Documents folder and select Properties. Note on the Target Folder Location, disitulah actual My Documents data is stored.
Storing the data in that location actually less safe, why?. If an error when the computer (can not go to Windows, for example) so that there is no other way to fix our computers, except with the Windows format, so difficult for us to save data such as My Documents located in the C, and so do the Windows format automatically all the data in the My Documents' will be erased. Windows format with the same remove 'all the data' in the drive / partition C.
It can still be saved for, among others, by copying the My Documents folder to another drive (such as drive D, E, etc.) through DOS, or move them through the hard copy (our hard drives installed in computers of others), but way above making enough for us. There is one trick that we can save the data in My Documents by moving the target location of My Documents to another partition, such as D, E, etc..
How easy enough, namely:
*
Right-click on Start and select Explore
*
In the partition / drive other than C (for instance in the drive / partition D), create a new folder with the name Dataku (or any other name as you)
*
Right-click on the My Documents folder and select Properties
*
Click the button Move .... In the box that appears, find the folder you created yesterday. If you have, click OK - OK. In my box appears, click Yes.
You can check:
The contents of the folder My Documents folder contents = Dataku (on the drive / partition D)
Thus, if an error when your computer should be in the Windows format, then all the My Document data will be safe because no longer stored on drive C, but has been moved to the drive D.
This is done considering the many people who have lost data, which are in the My Documents format done when Windows. If you do these tips, such as the incident was not to be on you.
Description:
*
Windows format is the process to reinstall Windows, in other words, your Windows replaced with a new 'total'
*
Drive / partition is a division of the location of hard drives for data storage in computers. If you open Windows Explorer, then usually be seen writing (C), (D), (E) and so forth. Parts of it useful to 'split' location data storage us. Unless the drive / partition to CD-ROM/DVD-ROM, the drive / partition is not working to save the data but work to read the chip CD / DVD
Please note that the location of 'original folder' My Documents from this are in the C: \ Documents and Settings \ User name \ My Documents. You can click through mengeceknya right in the My Documents folder and select Properties. Note on the Target Folder Location, disitulah actual My Documents data is stored.
Storing the data in that location actually less safe, why?. If an error when the computer (can not go to Windows, for example) so that there is no other way to fix our computers, except with the Windows format, so difficult for us to save data such as My Documents located in the C, and so do the Windows format automatically all the data in the My Documents' will be erased. Windows format with the same remove 'all the data' in the drive / partition C.
It can still be saved for, among others, by copying the My Documents folder to another drive (such as drive D, E, etc.) through DOS, or move them through the hard copy (our hard drives installed in computers of others), but way above making enough for us. There is one trick that we can save the data in My Documents by moving the target location of My Documents to another partition, such as D, E, etc..
How easy enough, namely:
*
Right-click on Start and select Explore
*
In the partition / drive other than C (for instance in the drive / partition D), create a new folder with the name Dataku (or any other name as you)
*
Right-click on the My Documents folder and select Properties
*
Click the button Move .... In the box that appears, find the folder you created yesterday. If you have, click OK - OK. In my box appears, click Yes.
You can check:
The contents of the folder My Documents folder contents = Dataku (on the drive / partition D)
Thus, if an error when your computer should be in the Windows format, then all the My Document data will be safe because no longer stored on drive C, but has been moved to the drive D.
This is done considering the many people who have lost data, which are in the My Documents format done when Windows. If you do these tips, such as the incident was not to be on you.
Description:
*
Windows format is the process to reinstall Windows, in other words, your Windows replaced with a new 'total'
*
Drive / partition is a division of the location of hard drives for data storage in computers. If you open Windows Explorer, then usually be seen writing (C), (D), (E) and so forth. Parts of it useful to 'split' location data storage us. Unless the drive / partition to CD-ROM/DVD-ROM, the drive / partition is not working to save the data but work to read the chip CD / DVD
Improving Computers Performance
Have a computer with a performance / performance of the fast, stable and optimal is something longed for each person. Trick following bagamana discuss how to improve computer performance. You can taste and proved, after a step-by-step tricks this, your computer will work faster than usual.
Settings done through the Registry editor / regedit. Therefore, before tips it is advisable to make a backup registry editor / backup registry editor. This is very useful to avoid a computer error / stuck due to errors in practice.
The steps to implement these tricks are as follows:
Set the Contiguous File Allocation Size
Trick is useful to improve the performance of the applications you use often. These include:
* Click Start - Run, then type: regedit
* Entrance to the HKEY_LOCAL_MACHINE \ System \ CurrentControlSet \ Control \ FileSystem
* Click on the right FileSystem folder and select New - DWORD Value. Give it a name with ContigFileAllooSize
* 2X Click the file ContigFileAllooSize was completed and the number 200 in its Value data.
Clear Memory Of DLL files
Trick is useful to the memory of the DLL files. Please note that the DLL files always take place for memory, even when programs that use file-fie your DLL has been closed, Windows still save them in memory. The way is:
* Click Start - Run, then type: regedit
* Entrance to the HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows \ CurrentVersion \ Explorer
* Right click on the Explorer folder and select New - String Value. Give it a name with AlwaysUnloadDll
* 2X Click the file and then enter AlwaysUnloadDll was number 1 in the Value data it.
* Restart the computer
Settings done through the Registry editor / regedit. Therefore, before tips it is advisable to make a backup registry editor / backup registry editor. This is very useful to avoid a computer error / stuck due to errors in practice.
The steps to implement these tricks are as follows:
Set the Contiguous File Allocation Size
Trick is useful to improve the performance of the applications you use often. These include:
* Click Start - Run, then type: regedit
* Entrance to the HKEY_LOCAL_MACHINE \ System \ CurrentControlSet \ Control \ FileSystem
* Click on the right FileSystem folder and select New - DWORD Value. Give it a name with ContigFileAllooSize
* 2X Click the file ContigFileAllooSize was completed and the number 200 in its Value data.
Clear Memory Of DLL files
Trick is useful to the memory of the DLL files. Please note that the DLL files always take place for memory, even when programs that use file-fie your DLL has been closed, Windows still save them in memory. The way is:
* Click Start - Run, then type: regedit
* Entrance to the HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows \ CurrentVersion \ Explorer
* Right click on the Explorer folder and select New - String Value. Give it a name with AlwaysUnloadDll
* 2X Click the file and then enter AlwaysUnloadDll was number 1 in the Value data it.
* Restart the computer
Turn off Your Computer with One Key of Keyboard
If we turn off the computer, usually done through the Start menu - Turn Off Computer, and the box that appears we select the Turn Off button, and then the computer will make the process of Shutdown. There is one more tips that we can turn off the computer only by pressing the button keyboard 1 so that it will improve our efficiency in the use of computers and accelerate the shutdown process itself.
To implement these tips, follow the steps as follows:
*
Right-click on the Desktop (main screen) and select Properties box that appears Display Properties
*
Select the Screen Saver tab and click the Power button ... so it appears the Power Options Properties.
*
Click the Advanced tab. In writing When I press the power button on my computer: the menu select Shut down. If you have, click the OK button - OK
To try it, please press the Power button on the keyboard (located right at the end of the indicator lights near the keyboard). You see, just by pressing buttons 1, the computer will immediately conduct Shut down the process.
To implement these tips, follow the steps as follows:
*
Right-click on the Desktop (main screen) and select Properties box that appears Display Properties
*
Select the Screen Saver tab and click the Power button ... so it appears the Power Options Properties.
*
Click the Advanced tab. In writing When I press the power button on my computer: the menu select Shut down. If you have, click the OK button - OK
To try it, please press the Power button on the keyboard (located right at the end of the indicator lights near the keyboard). You see, just by pressing buttons 1, the computer will immediately conduct Shut down the process.
Adding Capacity Memory / RAM With Flashdisk
Capacity memory / RAM, which can improve the performance of the computer itself. If you feel less, with a capacity of memory / RAM there, you can add them from the device to bring. Could. Virtual Memory, that is the answer. Adding capacity memory / RAM to bring this term is often called the Virtual Memory.
Virtual Memory is the 'additional memory' to anticipate if the data is in memory / RAM in the main is full.
The requirements that must exist is to bring the motherboard and must have USB 2.0 support, if still using a USB 1, the results obtained so less visible. Will be more than the maximum to bring more if you use the facilities have been using Ready boost. Initially, Ready boost is a facility for Windows Vista, but you can also do so in Windows XP (imitation Ready boost)
The way is as follows:
* Pair bring to the computer
* Right click on My Computer and select Properties
* Click the Advanced tab, then click the Settings button in the box Performance
* In the window that appears, click the Advanced tab and click the Change button in the Virtual memory
* Select the drive C, then select No paging file. If you have proceed by clicking the button Set
* Select the drives' bring 'you (such as drive F), usually given the name of the Removable disk if you do not give the name to bring it. Then select System managed size and by clicking the button Set
* Note padakotak Total paging file size for all drives. Recommended value should not exceed its capacity to bring
* If more then you can enter 'total value' of the capacity to bring. By the way, click the Custom Size option and the Initial Size and Maximum Size filled with a total value of the capacity to bring. You must be leaving a 5 - 6 Mb. This is a requirement of Windows XP itself. If you have, click the Set
* Click OK and then restart the computer
Virtual Memory is the 'additional memory' to anticipate if the data is in memory / RAM in the main is full.
The requirements that must exist is to bring the motherboard and must have USB 2.0 support, if still using a USB 1, the results obtained so less visible. Will be more than the maximum to bring more if you use the facilities have been using Ready boost. Initially, Ready boost is a facility for Windows Vista, but you can also do so in Windows XP (imitation Ready boost)
The way is as follows:
* Pair bring to the computer
* Right click on My Computer and select Properties
* Click the Advanced tab, then click the Settings button in the box Performance
* In the window that appears, click the Advanced tab and click the Change button in the Virtual memory
* Select the drive C, then select No paging file. If you have proceed by clicking the button Set
* Select the drives' bring 'you (such as drive F), usually given the name of the Removable disk if you do not give the name to bring it. Then select System managed size and by clicking the button Set
* Note padakotak Total paging file size for all drives. Recommended value should not exceed its capacity to bring
* If more then you can enter 'total value' of the capacity to bring. By the way, click the Custom Size option and the Initial Size and Maximum Size filled with a total value of the capacity to bring. You must be leaving a 5 - 6 Mb. This is a requirement of Windows XP itself. If you have, click the Set
* Click OK and then restart the computer
Friday, November 7, 2008
Free Portable Tools by Kaspersky AVZ Antiviral Toolkit
One of the drowning, which is quite popular Kaspersky. Although there is no free version of AntiVirus, they offer the online scanner (without facilities remover), a rescue disk and AVPTool, Antivirus removal. In addition, there is one more tools grati and Portable from Kaspersky, who called AVZ Antiviral Toolkit.
AVZ merupakan Antiviral Toolkit untuk menganalisa sistem dan recovery. Fungsi utamanya seperti Trojan Hunter atau Ad-Aware yang berarti untuk menghilangkan malwares dan bukan berfokus pada virus.
AVZ Antiviral toolkits in the design to detect and remove various malware such as the following:
* The various modules Spyware and adware
* Dialer (Trojan.Dialer)
* Various Trojan
* BackDoor
* Network Worm and email
* TrojanSpy, TrojanDownloader, Trojan Dropper.
In addition, this tool is equipped with various features such as the following:
* Heuristic firmware verification system, to check for the existence of viruses and spyware from the analysis registry, hard drives and memory
* Update database file security
* Integrated with rootkits detection system (malware that can not be seen with regular antivirus)
* Keylogger detection and Trojan DLL.
* Neyroanalizator, the ability to detect suspicious files with the technique Neura Network.
* Analysis of the Open Port TCP / UDP
* Integrated with Process Manager, services and Driver
* Facilities search the files with a variety of additional criteria.
* The ability to search data in the registry
* Some of the facilities to repair damage to the system, such as Internet Explorer settings, damage to software or system settings alinnya.
* Checks the archive file, such as zip, zip, cab, gzp, tar, mht and CHM.
* Script, which menungkinkan users define their own operations desired
* Process Analyzer, to search for the suspicious process in memory
* AVZGuard System, for protection from the way various applications, change the registry process and the other off.
* Walking to the file in the lock, with direct access to the system drive.
* Boot Driver Cleaner, to clean the system (files, drivers, registry key) from KernelMode.
* Various other facilities
Download AVZ Antiviral Toolkit here
adopted from :http://ebsoft.web.id/


AVZ merupakan Antiviral Toolkit untuk menganalisa sistem dan recovery. Fungsi utamanya seperti Trojan Hunter atau Ad-Aware yang berarti untuk menghilangkan malwares dan bukan berfokus pada virus.
AVZ Antiviral toolkits in the design to detect and remove various malware such as the following:
* The various modules Spyware and adware
* Dialer (Trojan.Dialer)
* Various Trojan
* BackDoor
* Network Worm and email
* TrojanSpy, TrojanDownloader, Trojan Dropper.
In addition, this tool is equipped with various features such as the following:
* Heuristic firmware verification system, to check for the existence of viruses and spyware from the analysis registry, hard drives and memory
* Update database file security
* Integrated with rootkits detection system (malware that can not be seen with regular antivirus)
* Keylogger detection and Trojan DLL.
* Neyroanalizator, the ability to detect suspicious files with the technique Neura Network.
* Analysis of the Open Port TCP / UDP
* Integrated with Process Manager, services and Driver
* Facilities search the files with a variety of additional criteria.
* The ability to search data in the registry
* Some of the facilities to repair damage to the system, such as Internet Explorer settings, damage to software or system settings alinnya.
* Checks the archive file, such as zip, zip, cab, gzp, tar, mht and CHM.
* Script, which menungkinkan users define their own operations desired
* Process Analyzer, to search for the suspicious process in memory
* AVZGuard System, for protection from the way various applications, change the registry process and the other off.
* Walking to the file in the lock, with direct access to the system drive.
* Boot Driver Cleaner, to clean the system (files, drivers, registry key) from KernelMode.
* Various other facilities
Download AVZ Antiviral Toolkit here
adopted from :http://ebsoft.web.id/


Tuesday, November 4, 2008
Making Yahoo Multi Messenger by Registry Editor
Yahoo Messenger (YM) is one of Messenger's most widely used to communicate via text online media (chat).
Normally you can only run one time YM at the same time. By following these tips you can run in several times so that at the same time you can log in using some of your yahoo account.
Here's the way you can follows:
1. Start the registry editor by clicking Start button - Run. Type regedit and press enter.
2. Entrance to the key HKEY_CURRENT_USER \ Software \ Yahoo \ Pager \ Test.
3. In the right panel, right-click menu and select New - DWord Value.
4. Type Plural.
5. Click on the 2x Plural and content with the value of one (1).
6. Exit from the registry editor.
If you follow the steps above the properly then you can run YM several times.
In addition to the above, you can download the file ym8multi.zip and 2x clicking on the settings in the registry. To restore the settings as you can download all ym8multi_unist.zip.
Tips on only for Yahoo Messenger version 8 you can download at http://messenger.yahoo.com/
Normally you can only run one time YM at the same time. By following these tips you can run in several times so that at the same time you can log in using some of your yahoo account.
Here's the way you can follows:
1. Start the registry editor by clicking Start button - Run. Type regedit and press enter.
2. Entrance to the key HKEY_CURRENT_USER \ Software \ Yahoo \ Pager \ Test.
3. In the right panel, right-click menu and select New - DWord Value.
4. Type Plural.
5. Click on the 2x Plural and content with the value of one (1).
6. Exit from the registry editor.
If you follow the steps above the properly then you can run YM several times.
In addition to the above, you can download the file ym8multi.zip and 2x clicking on the settings in the registry. To restore the settings as you can download all ym8multi_unist.zip.
Tips on only for Yahoo Messenger version 8 you can download at http://messenger.yahoo.com/
Friday, October 31, 2008
Windows 7 Will Be Released Soon
Vista may have advantages in terms of visual. However, the hardware needed to run the operating system this should have a greater specification. If executed with the hardware specifications of the low, the vista will be running slow. This makes users feel very uncomfortable.
To fix this version of Windows Vista, Microsoft re-released version of Windows 7, which reportedly is an improvement from the vista.
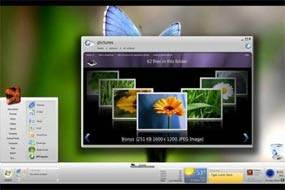
According to the news that outstanding, Windows Seven can be run with the specifications of the hardware that is not too large. Visual display is not lost from the vista. And the most incredible things on the windows 7, it has touch screen feature. Truly a breakthrough that is brilliant.
How Windows 7 will be booming in the market? Let's see it next year. Because the Windows 7 will be launched in 2010.
To fix this version of Windows Vista, Microsoft re-released version of Windows 7, which reportedly is an improvement from the vista.

According to the news that outstanding, Windows Seven can be run with the specifications of the hardware that is not too large. Visual display is not lost from the vista. And the most incredible things on the windows 7, it has touch screen feature. Truly a breakthrough that is brilliant.
How Windows 7 will be booming in the market? Let's see it next year. Because the Windows 7 will be launched in 2010.
Vista Security Make Comfortable, really??
Is vista not need to use additional antivirus program? Some time ago one of the leaders of Microsoft, Jim Allchin, Co-President of Microsoft, suggests it. He said the security features vista has been quite steady. According to the program evil will penetrate the security difficulties on each windows vista outstanding. Allchin admitted there will still be a threat to the security of vista, because it can not be ascertained. Is vista not need antivirus software? Allchin only imply that the security features in the vista beyond what is met by existing antivirus software current.
However, the fact that the security vista often making the user. This was also experienced by my own. When you want to run the game recently installed, always appearing box warning "crashes app ..." so that the game can not be executed. Even on the windows XP, the game can run smoothly. New security after the vista demolished and changed, the game can be started. So when making applications that we want to run can not be exercised so that we have to be clever to change the security setting on the vista.

However, the fact that the security vista often making the user. This was also experienced by my own. When you want to run the game recently installed, always appearing box warning "crashes app ..." so that the game can not be executed. Even on the windows XP, the game can run smoothly. New security after the vista demolished and changed, the game can be started. So when making applications that we want to run can not be exercised so that we have to be clever to change the security setting on the vista.
Caution Fake Login Yahoo!
Lately, rampant circulation of a link that when clicked will display the contents page false Yahoo account login. Caution your password rovered! The link can be derived from one of your brightness. It is vital It is vital to show an image, the victims trapped clicking the link will be transmitted on the Yahoo login page false, that pointed to the theft of user account information or a known familiar with Phishing.
If noted, the web page view is false is very similar to the Yahoo login page official web page installed on the false free web hosting provided by Yahoo, GeoCities. GeoCities hosting this election is also an astute pishing that because the recipient will not receive suspicious of GeoCities page autentifikasi Unsurprisingly, which is owned by Yahoo.
Without a bit suspicious, you may enter information directly username and password and click the button to sign in to see the photos your friends, without aware that the account information you have disadap other people. Come, pishing this action really does not make you suspicious because after I sign in, you will digiring to the web page yahoo photo
If noted, the web page view is false is very similar to the Yahoo login page official web page installed on the false free web hosting provided by Yahoo, GeoCities. GeoCities hosting this election is also an astute pishing that because the recipient will not receive suspicious of GeoCities page autentifikasi Unsurprisingly, which is owned by Yahoo.
Without a bit suspicious, you may enter information directly username and password and click the button to sign in to see the photos your friends, without aware that the account information you have disadap other people. Come, pishing this action really does not make you suspicious because after I sign in, you will digiring to the web page yahoo photo
Skype has Lies-Detector Feature
Skype users can now ensure that talking seriously or not. By utilizing the facilities KishKish Lie Detector made BATM Advanced Communications Ltd., Skype users can identify the recipient honesty.
How it works, this application will analyze the audio stream that is sent via real-time Skype calls. Then, this application will describe the stress level of the recipient users.
This product is also equipped with voice mail and call recorder to analyze the lie to several calls ago.
This Lies-Detector is a paying product of the latest popular tool. Unfortunately Skype does not explain how the price of this application and when the product is launched.
How it works, this application will analyze the audio stream that is sent via real-time Skype calls. Then, this application will describe the stress level of the recipient users.
This product is also equipped with voice mail and call recorder to analyze the lie to several calls ago.

This Lies-Detector is a paying product of the latest popular tool. Unfortunately Skype does not explain how the price of this application and when the product is launched.
Starting Business Without Money
1. Trust capital
Start a business without cash you can also do with a mediator. Become a mediator in the core is to sell information. Information is the heart to achieve success.
As the example by M. Suyanto, bussinessman from Indonesia told that he has a friend who called Mr. Ali, when he was a mediator when STMIK AMIKOM Yogyakarta buy land owned by PT. Djarum, which is located on the North Ring Road inclined Chess, Sleman in Yogyakarta, Indonesia. Area of land purchased STMIK AMIKOM Yogyakarta less than 6,000 square meters. Price per meter when the IDR. 275,000, -, the overall price of Rp. 1650000000, -. Mr. Ali received 2.5% of the total price as a mediator, namely Rp. 41250000, -. With the income to do so once a large transaction, a interpose the job is very interesting. Similarly when I sell the land in the area of Yogyakarta Monument Back, IDR. 220 million, as the friend I get Rp. 5.5 million from me. Not to my friends also get part of my land buyers. Good enough, isn't it??
2. Brain capital
Most of the people that I met with said that they want to open a business but do not have the capital. Even God does not give a capital tandingannya there, the "brain".
In his journal, M. Suyanto said that your brain is not more than seuntai wine, even smaller than a cabbage. Weighing less than 1.5 kg. However, the brain tell times more powerful than the computer of the world. I have fruit flies 100,000 brain cells active. I have 5 million rat brain cells. Animal primates 10 billion. Meanwhile, you have 100 billion brain cells active since birth. But you are very human indeed extraordinary. You do not have the capital can still open a business with your brain. One way to open the business without cash payment is the background and is a powerful weapon that was my life.
At the time we open a branch in the road Primagama Demangan Kidul number 92, the home of Mr. Sri Satoto. We open a business with the method of payment in the background. We say "Sir we will rent a house for a year, Mr.". "Please. I am happy to students such as you have activities, "Mr. Sri Satoto responsibility. "We will pay per month, Sir," we said. "No nothing," Mr. Sri Satoto responsibility. "But we will begin paying next month Pak." Mr Sri Satoto silent a moment, then said, "Yes. No nothing. " on the goodness of Mr Sri Satoto we are able to open branches without money and fully
Similarly when I founded STMIK AMIKOM Yogyakarta, with the brain, I've Mr Budi Sutrisno house that has a house on Jl. No Monginsidi. 8. "Mr Budi I will rent a house for two years .". "Oh please. The house is still empty "Mr Budi responsibility. "I will start to rent in March this Sir. But I will pay in August and September. " "Did so" Pak said Budi. "Because I do not have the money Sir. After the August and September, Insya Allah, I can earn money from students and that I will pay on Mr Budi. " Mr Budi silent a moment, then said, "Yes it does not matter, but I implore dinotariskan yes." "Yes Sir," I said. So, Academy of Management Information and Computer "AMIKOM" Yogyakarta, which is now a STMIK AMIKOM Yogyakarta can stand without cash. Now STMIK AMIKOM Yogyakarta have the land around 10,000 square meters and 2-storey building quite luxurious five floors and three entirely air-conditioned and the Wireless Fidelity (WI-FI), so that the students call such as shopping malls. These began with the brain, not with cash.
3. Capital hospitality
Success in the book Adventures, Roger Konopasek personality of a chef named Hussein calls. At a dinner at a restaurant where he worked, it alone. When will close the restaurant, Hussein saw a man walking towards the restaurant. See the restaurant will be closed, the man asked "Is there may be food-poor warm Australian tourist who lost in the middle of the city and hunger" ask the man. Without blinking, Hussein invite guests to sit and demand.
Returning from the kitchen, he found that both guests surprising that the two tables to sit as far from the tourist Australia. When Hussein spoke in English, guests will only sign of the shoulder does not understand. Guests can not speak English, but to give an explanation in Arabic. Because Hussein learn a little Arabic at a Koran school, he was able to guess that the man was from Saudi Arabia, lost in the city and very hungry. Hussein returned to the kitchen and prepare food fresh for the second time. Returning to the dining room, he felt sad that silence. Two men sitting in the empty restaurant in the middle of the night silence is very sad. Hussein finally decided untukmenghibur second with guests sitting in between them, using English and Arabic silih bergani. After several minutes involved in the conversation, he found something interesting. Wed have the export-import business and is in its first trip to this region to search for new transactions. While the men Australiaadalah sheep ranch that big. At the time Hussein tried to connect them. Hussein asked whether Australia's men intend to export sheep to the Arabs. He answers the form of pitching the full spirit. Then he returned to Arab men and asked whether he was interested to import fresh sheep for a delicious business Aji when hundreds of thousands of people met in Saudi Arabia for the pilgrimage to the holy places. Once again, Hussein answers the form of pitching the full spirit.
Hobbes three-way conversation to be more alive. They exchange addresses, negotiating prices and bank account numbers written on a napkin. After two hours menerjemehkan and negotiate, both the guests shake hands, pat each other shoulders and say farewell to Hussein. Three months later, Hussein's open letter from the Australian men. Men are grateful because the translator Hussein to be a good watcher and sharp-eyed business. In the letter, Hussein get a check worth $ 20,000, which is part of the agreement. Friendliness and openness to change his life to become hawk-eyed watcher business.
Start a business without cash you can also do with a mediator. Become a mediator in the core is to sell information. Information is the heart to achieve success.
As the example by M. Suyanto, bussinessman from Indonesia told that he has a friend who called Mr. Ali, when he was a mediator when STMIK AMIKOM Yogyakarta buy land owned by PT. Djarum, which is located on the North Ring Road inclined Chess, Sleman in Yogyakarta, Indonesia. Area of land purchased STMIK AMIKOM Yogyakarta less than 6,000 square meters. Price per meter when the IDR. 275,000, -, the overall price of Rp. 1650000000, -. Mr. Ali received 2.5% of the total price as a mediator, namely Rp. 41250000, -. With the income to do so once a large transaction, a interpose the job is very interesting. Similarly when I sell the land in the area of Yogyakarta Monument Back, IDR. 220 million, as the friend I get Rp. 5.5 million from me. Not to my friends also get part of my land buyers. Good enough, isn't it??
2. Brain capital
Most of the people that I met with said that they want to open a business but do not have the capital. Even God does not give a capital tandingannya there, the "brain".
In his journal, M. Suyanto said that your brain is not more than seuntai wine, even smaller than a cabbage. Weighing less than 1.5 kg. However, the brain tell times more powerful than the computer of the world. I have fruit flies 100,000 brain cells active. I have 5 million rat brain cells. Animal primates 10 billion. Meanwhile, you have 100 billion brain cells active since birth. But you are very human indeed extraordinary. You do not have the capital can still open a business with your brain. One way to open the business without cash payment is the background and is a powerful weapon that was my life.
At the time we open a branch in the road Primagama Demangan Kidul number 92, the home of Mr. Sri Satoto. We open a business with the method of payment in the background. We say "Sir we will rent a house for a year, Mr.". "Please. I am happy to students such as you have activities, "Mr. Sri Satoto responsibility. "We will pay per month, Sir," we said. "No nothing," Mr. Sri Satoto responsibility. "But we will begin paying next month Pak." Mr Sri Satoto silent a moment, then said, "Yes. No nothing. " on the goodness of Mr Sri Satoto we are able to open branches without money and fully
Similarly when I founded STMIK AMIKOM Yogyakarta, with the brain, I've Mr Budi Sutrisno house that has a house on Jl. No Monginsidi. 8. "Mr Budi I will rent a house for two years .". "Oh please. The house is still empty "Mr Budi responsibility. "I will start to rent in March this Sir. But I will pay in August and September. " "Did so" Pak said Budi. "Because I do not have the money Sir. After the August and September, Insya Allah, I can earn money from students and that I will pay on Mr Budi. " Mr Budi silent a moment, then said, "Yes it does not matter, but I implore dinotariskan yes." "Yes Sir," I said. So, Academy of Management Information and Computer "AMIKOM" Yogyakarta, which is now a STMIK AMIKOM Yogyakarta can stand without cash. Now STMIK AMIKOM Yogyakarta have the land around 10,000 square meters and 2-storey building quite luxurious five floors and three entirely air-conditioned and the Wireless Fidelity (WI-FI), so that the students call such as shopping malls. These began with the brain, not with cash.
3. Capital hospitality
Success in the book Adventures, Roger Konopasek personality of a chef named Hussein calls. At a dinner at a restaurant where he worked, it alone. When will close the restaurant, Hussein saw a man walking towards the restaurant. See the restaurant will be closed, the man asked "Is there may be food-poor warm Australian tourist who lost in the middle of the city and hunger" ask the man. Without blinking, Hussein invite guests to sit and demand.
Returning from the kitchen, he found that both guests surprising that the two tables to sit as far from the tourist Australia. When Hussein spoke in English, guests will only sign of the shoulder does not understand. Guests can not speak English, but to give an explanation in Arabic. Because Hussein learn a little Arabic at a Koran school, he was able to guess that the man was from Saudi Arabia, lost in the city and very hungry. Hussein returned to the kitchen and prepare food fresh for the second time. Returning to the dining room, he felt sad that silence. Two men sitting in the empty restaurant in the middle of the night silence is very sad. Hussein finally decided untukmenghibur second with guests sitting in between them, using English and Arabic silih bergani. After several minutes involved in the conversation, he found something interesting. Wed have the export-import business and is in its first trip to this region to search for new transactions. While the men Australiaadalah sheep ranch that big. At the time Hussein tried to connect them. Hussein asked whether Australia's men intend to export sheep to the Arabs. He answers the form of pitching the full spirit. Then he returned to Arab men and asked whether he was interested to import fresh sheep for a delicious business Aji when hundreds of thousands of people met in Saudi Arabia for the pilgrimage to the holy places. Once again, Hussein answers the form of pitching the full spirit.
Hobbes three-way conversation to be more alive. They exchange addresses, negotiating prices and bank account numbers written on a napkin. After two hours menerjemehkan and negotiate, both the guests shake hands, pat each other shoulders and say farewell to Hussein. Three months later, Hussein's open letter from the Australian men. Men are grateful because the translator Hussein to be a good watcher and sharp-eyed business. In the letter, Hussein get a check worth $ 20,000, which is part of the agreement. Friendliness and openness to change his life to become hawk-eyed watcher business.
Blue Ocean Strategy
Strategies to compete in the competition is very tight can cause "sea of blood" for companies that compete or are put-off. This strategy is known as Bloody or Red Ocean Strategy. W. Chan Kim and Renee Mauborgne said that the Red Ocean Strategy is no longer effective to create growth and profits in the future. They are proposing a new strategy called the Blue Ocean Strategy. Differences between the Red Ocean Strategy and Blue Ocean Strategy, among others, on to the market, competition, demand, values and strategy.
Red Ocean Strategy considers that to compete it is to compete in the market space that, while the Blue Ocean Strategy, considers that compete is to create market space that is not their. The market is very broad bagaiakan "blue ocean". Because the market is very broad, companies can choose the market as the heart. Red Ocean Strategy to use the concept can grow and benefit with the defeat competitors in the competition. Blue Ocean Strategy by using the concept to create competition that does not exist. Because there is no competition, the only company to compete with himself without another company. The company will win the competition unopposed. Red Ocean Strategy exploit the demand that exists limitless. Blue Ocean Strategy to create and capture new demand. Red Ocean Strategy to achieve excellence create value, then the Blue Ocean Strategy to achieve excellence without the need to create value. Red Ocean Strategy unified system with the overall activities of the company by selecting a differentiation strategy or overall cost leadership strategy (the low-cost strategy), while the Blue Ocean Strategy unified system with the overall activities of the company in implementing the strategy and differentiation strategy of leadership in the overall cost of co - same. Blue Ocean Strategy myangkut two aspects. First, how to find and develop the blue ocean. To find and develop the blue ocean, with the launch of new industries such as a complete eBay auction conducted on the Internet and do more with the general idustri expand the boundaries created by the red ocean. Second, how mengekploitasi and protect the blue ocean.
The competition is killed off and the other (red ocean strategy) should be replaced with or without persaing competition without having to kill (the blue ocean strategy), so the business is to be beautiful. "Therefore, we set (a law) for the Banu Israil, that he who kills one, not because the person is (kill) other people, or because not corrupt in the earth, then as if he has killed all mankind . And anyone who maintain the life of a human being, then as if he has been maintaining all human life ... .. (Al-Maidah paragraph 32).
Red Ocean Strategy considers that to compete it is to compete in the market space that, while the Blue Ocean Strategy, considers that compete is to create market space that is not their. The market is very broad bagaiakan "blue ocean". Because the market is very broad, companies can choose the market as the heart. Red Ocean Strategy to use the concept can grow and benefit with the defeat competitors in the competition. Blue Ocean Strategy by using the concept to create competition that does not exist. Because there is no competition, the only company to compete with himself without another company. The company will win the competition unopposed. Red Ocean Strategy exploit the demand that exists limitless. Blue Ocean Strategy to create and capture new demand. Red Ocean Strategy to achieve excellence create value, then the Blue Ocean Strategy to achieve excellence without the need to create value. Red Ocean Strategy unified system with the overall activities of the company by selecting a differentiation strategy or overall cost leadership strategy (the low-cost strategy), while the Blue Ocean Strategy unified system with the overall activities of the company in implementing the strategy and differentiation strategy of leadership in the overall cost of co - same. Blue Ocean Strategy myangkut two aspects. First, how to find and develop the blue ocean. To find and develop the blue ocean, with the launch of new industries such as a complete eBay auction conducted on the Internet and do more with the general idustri expand the boundaries created by the red ocean. Second, how mengekploitasi and protect the blue ocean.
The competition is killed off and the other (red ocean strategy) should be replaced with or without persaing competition without having to kill (the blue ocean strategy), so the business is to be beautiful. "Therefore, we set (a law) for the Banu Israil, that he who kills one, not because the person is (kill) other people, or because not corrupt in the earth, then as if he has killed all mankind . And anyone who maintain the life of a human being, then as if he has been maintaining all human life ... .. (Al-Maidah paragraph 32).
Tuesday, October 21, 2008
Create A Super-hidden Attribute
Virus usually do this intentionally. But now you can also create a super-hidden attributes.
The meaning of super-hidden attribute is an attribute to hide files or folders that are not shown in the Windows Explorer, although the show hidden files has been activated. Here's how:
1. Go to DOS by clicking the Start | run...| and then type cmd | ok
2. After entry the DOS window, go to the drive where the files or folders that will be super-hidden attributes. For example, from drive C: move to drive D: , type D: . Then click Enter
3. If the file is located in the folder or directory, you must first enter into the folder. Type cd foldername
4. After finding the file that will be super hiden attribute, type the command
attrib
5. So if you see in the windows explore, the files are missing or will not appear although show hidden files is activated
6. to make super-hidden attribute folder on almost the same but given a little extra, so a command be attrib
The meaning of super-hidden attribute is an attribute to hide files or folders that are not shown in the Windows Explorer, although the show hidden files has been activated. Here's how:
1. Go to DOS by clicking the Start | run...| and then type cmd | ok
2. After entry the DOS window, go to the drive where the files or folders that will be super-hidden attributes. For example, from drive C: move to drive D: , type D: . Then click Enter
3. If the file is located in the folder or directory, you must first enter into the folder. Type cd
4. After finding the file that will be super hiden attribute, type the command
attrib
5. So if you see in the windows explore, the files are missing or will not appear although show hidden files is activated
6. to make super-hidden attribute folder on almost the same but given a little extra, so a command be attrib
Create A Folder Without A Name
Usually, when we create a folder so that the folder should be given a name. The default of folder name is New Folder. However, we can create a folder without a name.
Try this :
Create a folder by click file | New | Folder
Then change the name New Folder by right clicking on the folder Rename
While pressing ALT write the number 0160 by using keypad numeric or part on the right keyboard ( [ALT] + [0160] ). Then click Enter
The actual number 0160 is characters a space that is hidden.
So now you have a folder without a name.
Well, hopefully useful. ^_^
Try this :
Create a folder by click file | New | Folder
Then change the name New Folder by right clicking on the folder Rename
While pressing ALT write the number 0160 by using keypad numeric or part on the right keyboard ( [ALT] + [0160] ). Then click Enter
The actual number 0160 is characters a space that is hidden.
So now you have a folder without a name.
Well, hopefully useful. ^_^
Track the IP Address using Yahoo! Messenger
Did you know? When we use Yahoo! Messenger, we can actually know the IP address of the opponent we chat
This is what we can do :
Firstly, send a file to the opponent we chat. And then go to the Command Prompt and type NETSTAT-N and press enter, then the IP address of your opponent's chat that you send file will appear with former port used for sending files.
To know the location of your opponent chat (real address), you can check it in www.domainwhitepages.com by using the IP address that you get.
It's so simple, isn't it?
This is what we can do :
Firstly, send a file to the opponent we chat. And then go to the Command Prompt and type NETSTAT-N and press enter, then the IP address of your opponent's chat that you send file will appear with former port used for sending files.
To know the location of your opponent chat (real address), you can check it in www.domainwhitepages.com by using the IP address that you get.
It's so simple, isn't it?
Subscribe to:
Comments (Atom)
